Managing Cluster Access in Loft
The core feature of Loft is to enable users to get self-service access to Kubernetes and allow them to create isolated namespaces and virtual clusters whenever they need them.
Working with Cluster Access
Create Cluster Access For Individual Users
- If you are still impersonating, click
- Go to the Clusters view using the main menu on the left
- Switch to the tab Cluster Access
- Click on the button
- Use the field Display Name and enter a Name for the cluster access
- In the Users & Teams section, make sure the Users tab is selected because we want to give an individual user access to a cluster
- Use the field Select Individual Users and select the User(s) you want to create this cluster access for
- In the Clusters section, either select All Clusters or the specific cluster that you want to make accessible for the user(s) you selected in the previous step
- Click the button at the bottom of the drawer
Single Sign-On + Cluster Access
You can connect a variety of SSO providers to Loft. To automatically give users access to clusters based on their SSO user groups, you can switch to the
Team Members
tab to grant cluster access for each member of a team (e.g. for each member of a group in Active Directory, Okta, SAML, etc.)Configuration
Metadata
Display Name
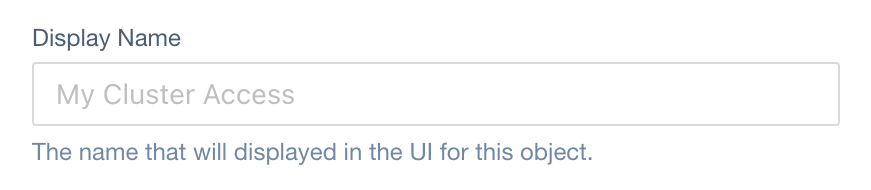
JSONPath in ClusterAccess CRD:
spec.displayName (type: string)
Kubernetes Name
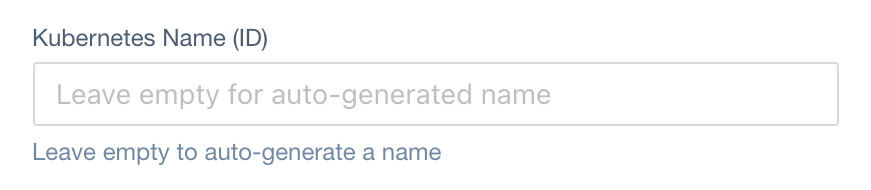
JSONPath in ClusterAccess CRD:
metadata.name (type: string)
Description

JSONPath in ClusterAccess CRD:
spec.description (type: string)
Labels

JSONPath in ClusterAccess CRD:
metadata.labels (type: map[string]string)
Annotations

JSONPath in ClusterAccess CRD:
metadata.annotations (type: map[string]string)
Users & Teams
Individual Users
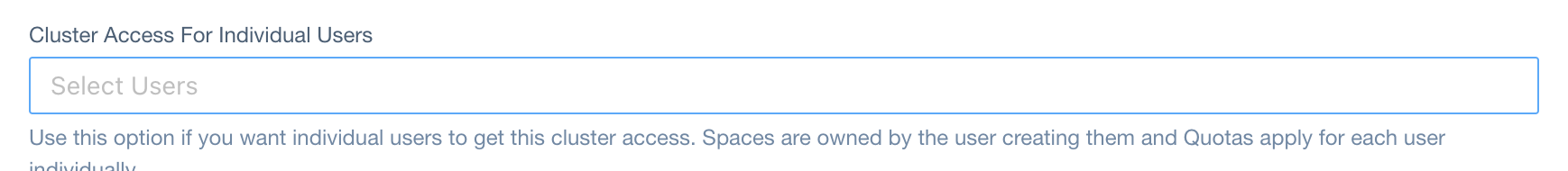
JSONPath in ClusterAccess CRD:
spec.users[].user (type: string)
Users In Teams
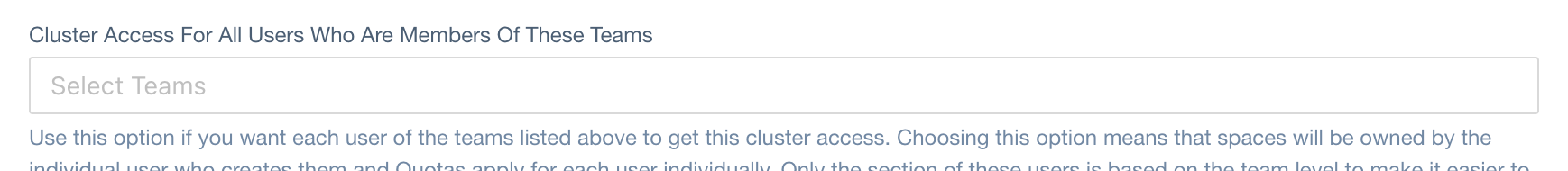
JSONPath in ClusterAccess CRD:
spec.users[].team (type: string)
Teams
JSONPath in ClusterAccess CRD:
spec.teams (type: string[])
Clusters
JSONPath in ClusterAccess CRD:
spec.clusters (type: string[])
Enforce Restrictions
Space Constraints
JSONPath in ClusterAccess CRD:
spec.spaceConstraintsRef (type: string)
Quotas

JSONPath in ClusterAccess CRD:
spec.quota (type: AccessQuota)
Advanded Options
Priority
JSONPath in ClusterAccess CRD:
spec.priority (type: integer)
Extra Cluster Roles
JSONPath in ClusterAccess CRD:
spec.clusterRoles[].name (type: string)
Access To Cluster Access
JSONPath in ClusterAccess CRD:
spec.access (type: Access[])